With a easy to use User Interface this malware generator enables unskilled wannabe criminals to unleash their own flavour of ransomware is a few clicks.
Variations of the WYSIWYE (What You See Is What You Encrypt) malware have been detected by Panda Security in companies across Europe, including Germany, Belgium, Sweden, and Spain.
Using an exploit through the Windows Remote Desktop Protocol technology, as explained in a blog post by Panda Security here, this ransomware infects corporate networks.
Credentials are obtained through a brute-force attack on the Remote Desktop Protocol, hackers are then in a position to unleash the malware.
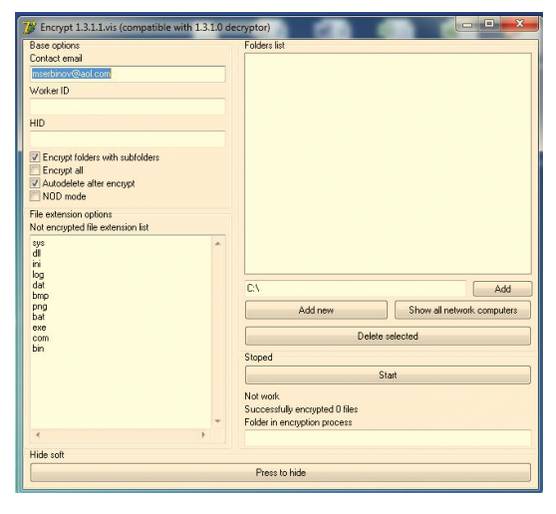
What You See Is What You Encrypt ransomware GUI [source: Panda Labs blog]
The User Interface makes it easy to run custom attacks. “With this customised attack, it’s possible to hand-pick the network computers whose information the attacker would like to encrypt, choose files, self-delete upon completing the encryption, enter stealth mode, etc.,” Panda Security explains.
The Spanish security firm sees this as part of a broader Ransomware-as-a-Service trend, which involves hosting affiliate programs and more.
Luis Corrons, PandaLabs technical director said, “crooks are demanding a minimum of €500 after each successful infection”.
“The tool is targeting criminals with no qualms,”Corrons said. “Expertise is no required, you don’t need an army of ransomware writers, just a bunch of them feeding the cybercriminal ecosystem”.
“There are hundreds of thousands of computers waiting to be compromised, listening to the RDP port in the open internet,” he added.
Another reason to keep all passwords, even internal ones as secure as possible.
And remember recent offline backups save you time and money should you be hit.
Check out our useful products to help combat ransomware.

